Persist Private IP in AWS Auto Scaling Group
Recently, we were moving our web application, which was on a single EC2 instance, to a highly available and fault-tolerant architecture. For that, we decide to pre-bake AMI and launch it with in an auto-scaling group and attach it to the target group behind an elastic load balancer. We had another server which was in the same VPC but not in the target group behind ELB. Requirements were to access our web application (single EC2 instance we launched using ASG and attached to ELB) privately within VPC due to HIPAA regulatory compliance.
In other words, we needed a way to persist a private IP to EC2 instance in case of scale in or scale out event. We did some research and came up with the solution to create the instance launch life cycle event. Capture the event using AWS CloudWatch Rules, and use AWS Lambda as a target to attach secondary ENI to new launched EC2 Instance in Auto Scaling Group.
Thanks to AWS knowledge center, we were able to modify their solution as per our needs.
But How Does It Work? 🤔
We needed a way to give secondary ENI description to lambda so that it can attach specific ENI to the newly launched instance. Therefore, we decided to get the description of ENI from EC2 instance tag. For that, we created a launch configuration for the auto scaling group with the tag named Eth1. And, give it a value which in actual is the description of secondary ENI.
1. Create life cycle hook on EC2 instance launch event.
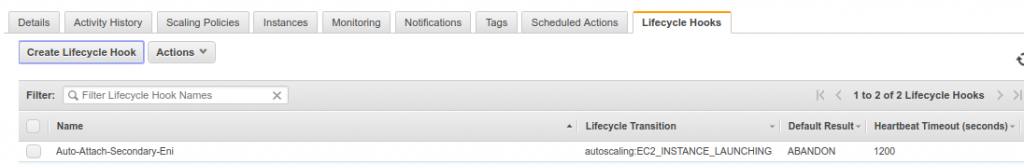
2. Creating AWS Cloud Watch Rule with target as a lambda.
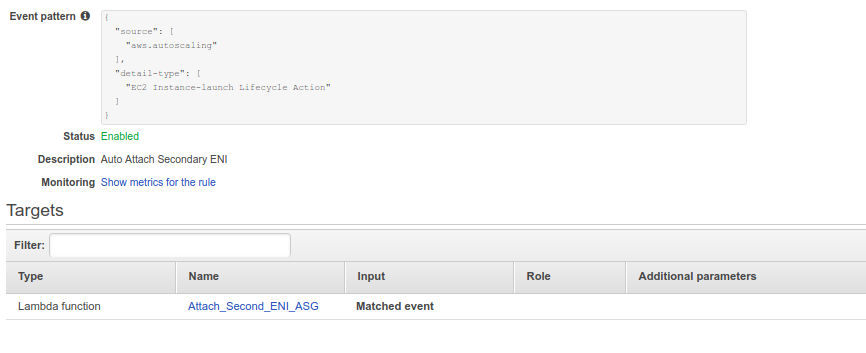
Here is the code to Lambda
https://github.com/MrHassanMurtaza/aws-attach-secondary-eni-lambda
Feel free to contribute and change as per your needs.
Leave a Reply